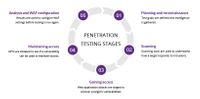
Penetration Testing- Ethical Hacking
Seien Sie dem Angreifer einen Schritt voraus.
Schützen Sie Ihre IT Infrastruktur durch gezielte Tests und schliessen Sie Lücken, bevor diese durch unsichtbare Angreifer ausgenutz werden.
Due Diligence
Kaufen Sie keine Katze im Sack.
Lassen Sie vor dem Vertragsabschluss bei Kaufprozessen den Käufer einer Sorgfaltsprüfung unterziehen.
Open Source Background Screening
Wissen Sie immer mit wem Sie es zu tun haben?
Lassen Sie relevante Personen vor dem ersten Meeting durch Open Source Checks prüfen. Unter Berücksichtigung der Datenschutzbestimmungen, erhalten Sie nach der Datensammlung einen Zusammenfassenden Bericht.
Weitere Dienstleistungen
- Cyber Security Risk Assessments
- Deep and Dark Web Monitoring
- IT-Forensik
- Linux Network Settings